Veriato Recon combines machine learning and advanced statistical analysis to uncover indicators of compromise traditional preventative security measures miss, so you can protect your organization from insider attacks
Behavioral Baselines
The software learns the behavior patterns in your company, and evaluates changes versus historical self and peer groups.

Anomaly Detection
Changes in behavior are identified in near real-time, and compared to sensitivity settings you control for prioritization.

Actionable Intelligence
Alerts are triggered on anomalies most indicative of insider threat in your organization, and rich activity data is stored for rapid review.
Your organization is, and will be, compromised by insiders.
Regardless of industry or company size, the fact is that people have become the perimeter. If you are not specifically looking for insider attacks, you are missing them. Veriato Recon combines analysis of technical indicators and psycholinguistic indicators to provide early warning of threats to your data security. An attacker, no matter how sophisticated, will cause a deviation from established patterns.
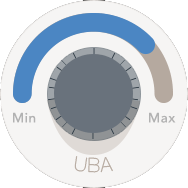
Elegantly Simple Tuning
Provides you with the ability to alert on meaningful behavioral changes, without contributing to over-alert syndrome.
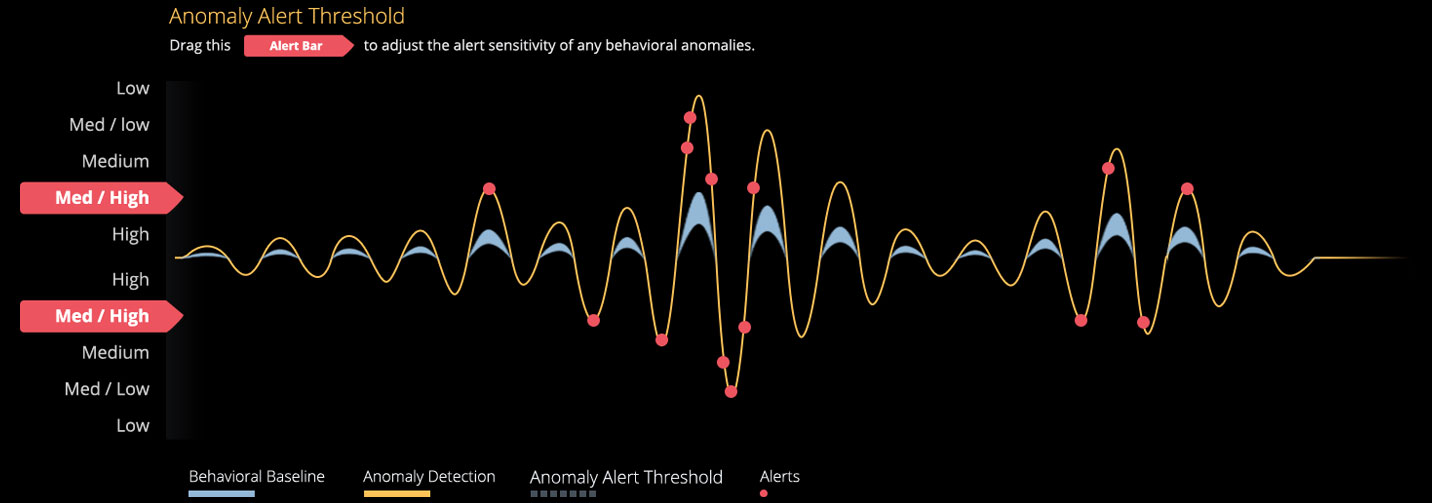


 Indicators of Compromise
Indicators of Compromise Psycholinguistic Attributes
Psycholinguistic Attributes