Veriato Investigator installs quickly, records detailed information on employee activity, and enables fast, accurate, and efficient exploration and playback of the recorded data. Veriato employee investigation software provides the answers you need so informed decisions get made.

Get Accurate Evidence
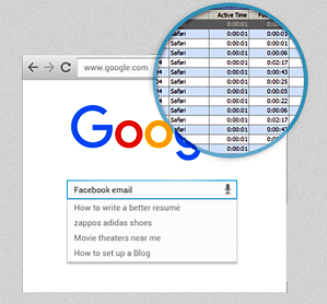
Veriato employee investigation software automatically records all computer activity, creating a record that can be used as evidence in civil and criminal litigation.
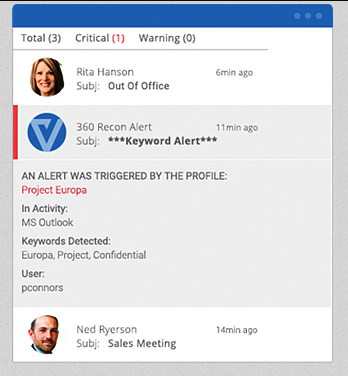
Anomaly Detection
Veriato Investigator’s invisible agent is deployed silently and managed from a remote console, so the target of the investigation is not alerted.

Actionable Intelligence
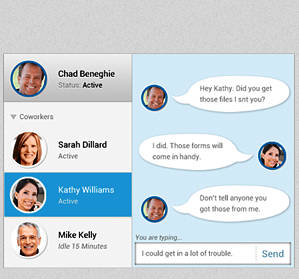
Recordings are centrally encrypted, stored and password protected, ensuring only appropriate eyes access and view the data.