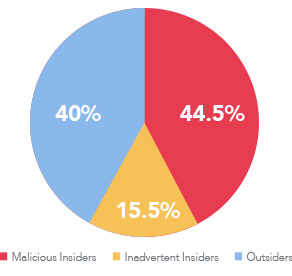
60% of Cyber Attacks Were Carried out by Insiders
Breach Source
In a recent 451 Research survey, insider threats ranked as the 2nd highest cybersecurity concern and the fastest growing among organizations.
Cost Per Incident
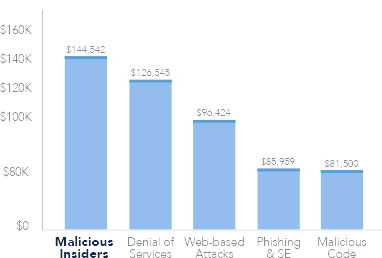
Businesses are more vulnerable to these attacks because traditional security investments fail to detect insider threats.



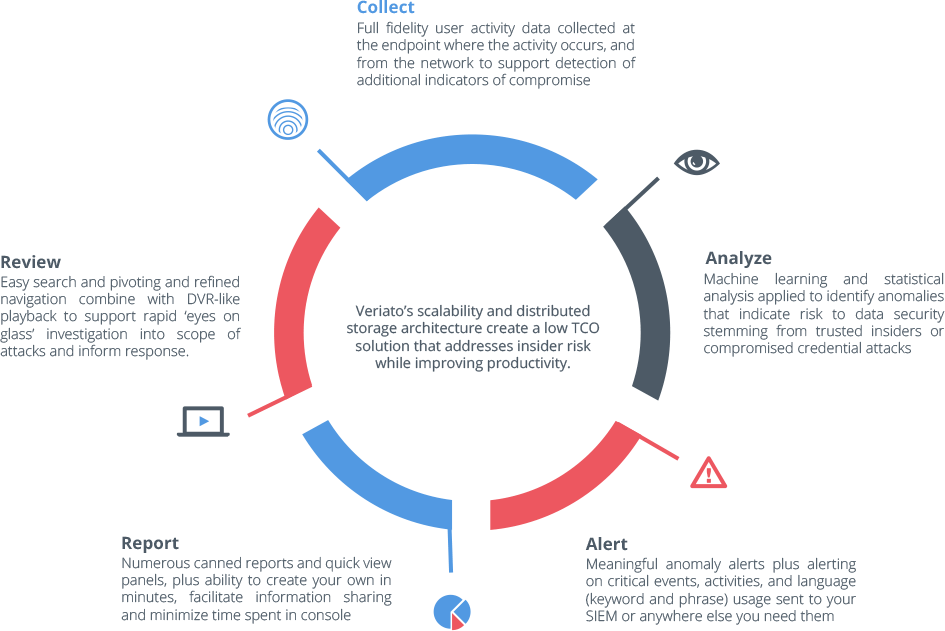
 Analyze a wide range of activity
Analyze a wide range of activity Detect indicators of compromise
Detect indicators of compromise